ZENworks patch policies were introduced in version 11.3 as a way for Administrators to express their wishes for automated patching. Judging by your feedback at Brainshare 2014, these are becoming very popular. Several of you asked questions about how to manually apply patch policies for devices that are mission critical e.g servers running SQL databases. The scenario is
“Tell me automatically what vulnerabilities exist but I want to manually apply the policy to remediate them”
Lets start with reminding ourselves what a patch policy is.
Patch policy: A set of rules that determine what vulnerabilities should be remediated.
These are defined in ZCC. Click on Patch Management and then click on Patch Policies
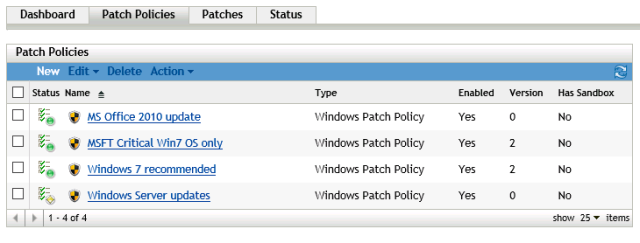
List of patch policies
To create a Patch Policy, click on New. Choose your platform and give the policy a name. Then you need to decide which vulnerabilities you want to remediate. This is achieved by using rules
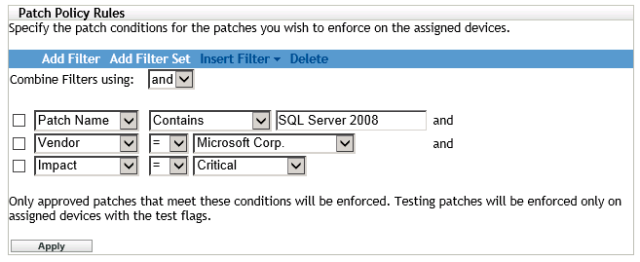
Patch policy rules
You can build up a fairly complex query to exactly determine the vulnerabilities you are interested in. At any time, click on Apply to see what the result will be.
Carry on and complete the Patch Policy. It will be added to the list shown in the first screen shot.
It could be that not all of the patches in the patch policy have not yet been cached ( downloaded ) into your zone. Either wait for the next download as per your patch download schedule or trigger one manually using ZCC -> Configuration -> Patch management -> Subscription service information and click on Update Now
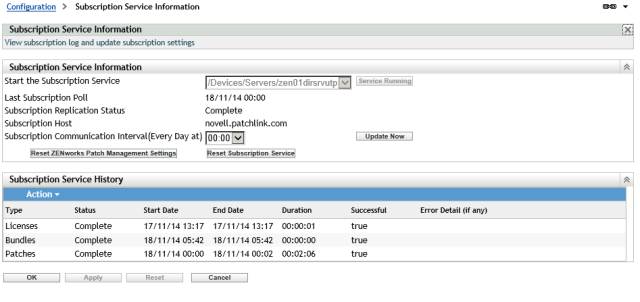
You also need to make sure that the patches are replicated to any primary / satellite servers used by those critical devices for content delivery. If you don’t do this, then the patch policy will fail as the required patches are not available for the target devices.
At this point you would apply the patch policy to devices that you want to automatically remediate those vulnerabilities. However, in this case we want to manually remediate.
Lets stop those devices from ever applying a patch policy by themselves. For the purposes of this post, I am assuming that you have all of those devices in their own Device Folder. If not, you’ll need to go to each Device in ZCC and change the settings.
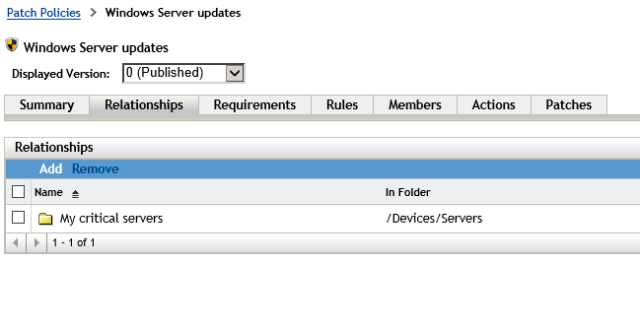
I have a device folder called ‘My critical servers’. To change the way Patch Policies are used for devices in that folder, click on Details
Folder details
In Details, click on Settings
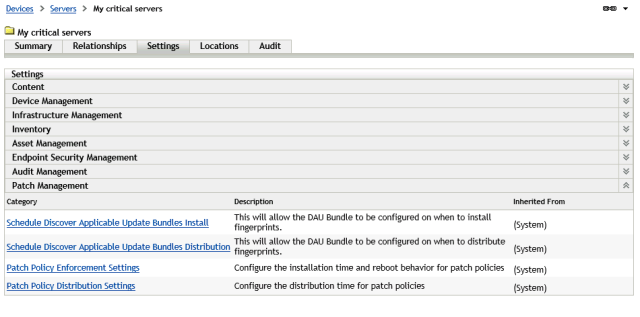
Settings
We need to alter Patch Policy Distribution and Patch Policy Enforcement. Let us start with Patch Policy Distribution
Click on Override. I would recommend that distribution of patches to devices is triggered when we manually remediate. You are free to choose a scheduled approach if that works better for your environment. Even if the patches have not yet arrived when you manually remediate, they will be downloaded. Remember to click on Ok when you have made any changes.
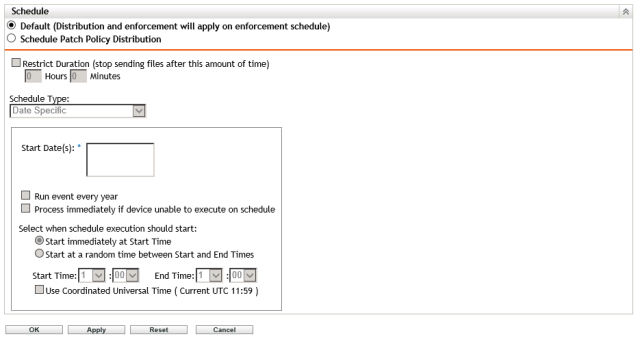
Now for Patch Policy Enforcement. This needs to be manual and not automatic.
As these are critical devices, disable automatic reboots. You can choose to reboot at your leisure. Just don’t leave it too long!
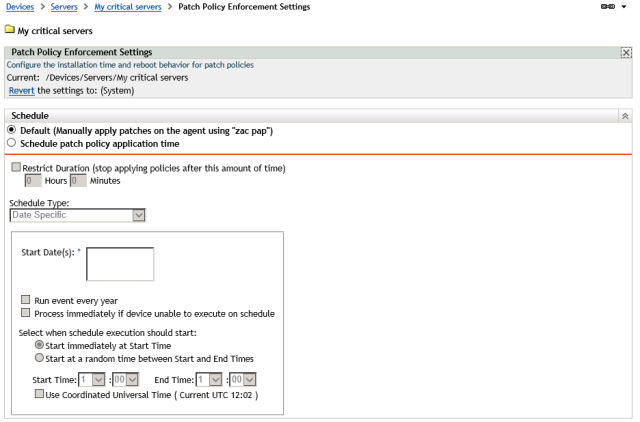
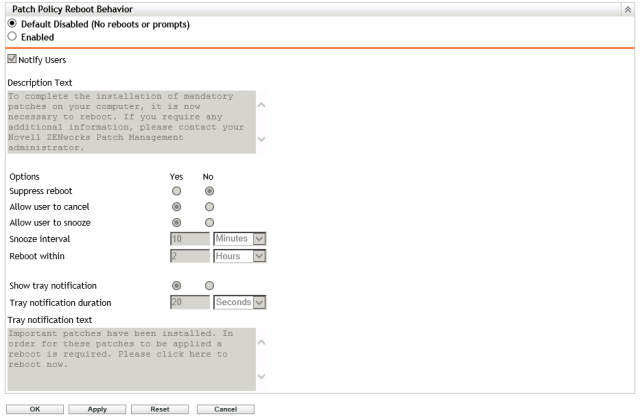
Click on Ok
And we’re almost there.
Go back to ZCC – Patch Management -> Patch policies. Click on the patch policy you want and then click on Relationships. Click Add and browse to the folder that contains your critical servers. If the patch policy is applicable to other devices, you can add those as well.
 To manually apply remediation, go to each device ( or remote control it ) and get to a command prompt. I would recommend that you run the command prompt as an administrator.
To manually apply remediation, go to each device ( or remote control it ) and get to a command prompt. I would recommend that you run the command prompt as an administrator.
To manually remediate vulnerabilities, as defined by the patch policy, we will take advantage of them using the ZENworks bundle feature.
“Hang on a minute” , I hear you say, ” What about zac pap? “
Two reasons
1 ) It is the worse acronym ever in ZENworks as shown by this entry from a U.K dictionary of slang
Noun. 1. Nonsense, rubbish.
2. Faeces.
Verb. To defecate. E.g.”He was so scared he papped his pants.”
2) zac pap applies all patch policies not just the one we are interested in. You may have another patch policy that the device has been included in. We only want to apply our patch policy.
Let press on.
At the command prompt, type zac bl
You will get a list of associated bundles for the device. In that list will be our patch policy.
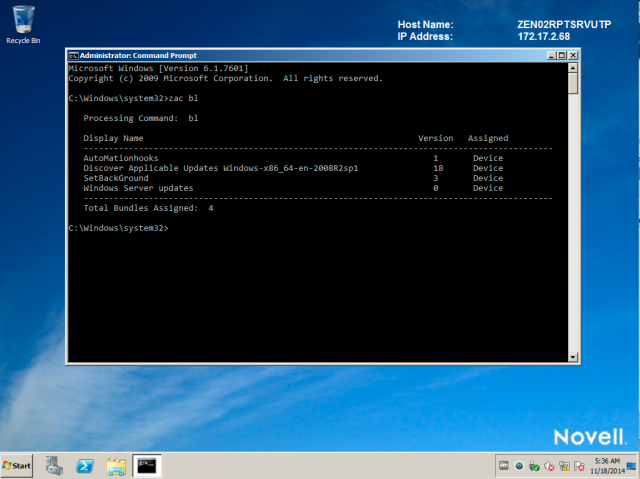
My patch policy is “Windows Server updates”
To apply the patches in that patch policy and remediate vulnerabilities, type zac bin <Display name shown in the list.>
If the patches have not yet been distributed, they will be. Once all patches are downloaded, installation will start
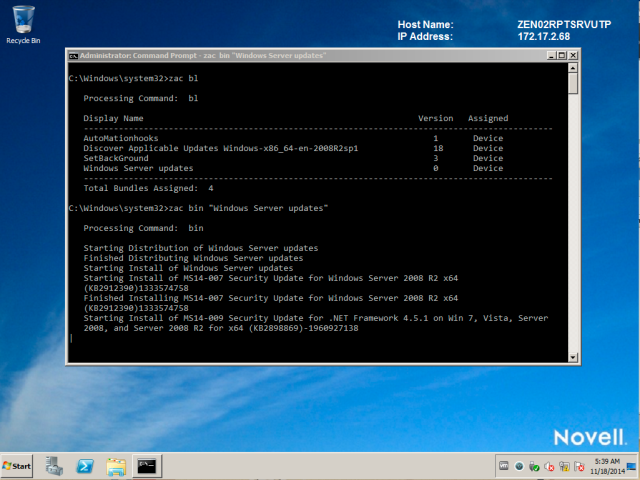
Wait until this process is completed.
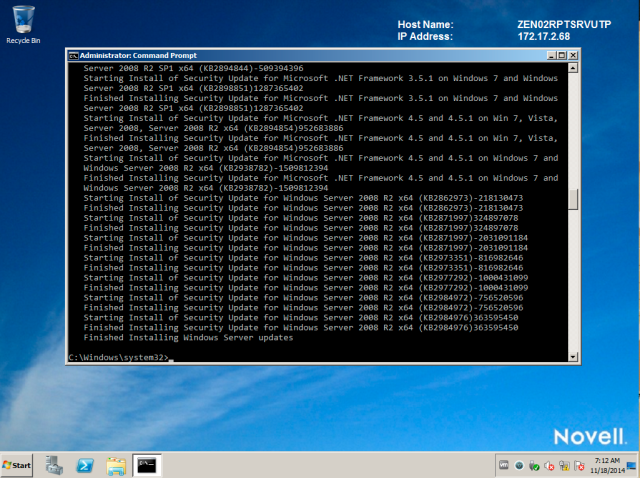
Then reboot when you’re ready.















